PrivacyX newsletter #2 Ransomware continues to exact a hard cost
The impact of ransomware continues to rise. In this newsletter I take a look at this growing cyber risk, what guidance is available to help, how regulators are reacting and what role AI will play.
Welcome to issue #2
Thanks again for all the feedback on about issue #1 on Global AI Policy, it was great to get the newsletter kicked off with this topic and I look forward to returning to AI policy in future issues. If you’re a new reader with this newsletter, there is some background about PrivacyX Consulting and my other work at the start of issue #1.
As before, this newsletter represents my own personal views and does not represent any of the organisations I work with.
This month I take a look at the rising profile of ransomware as a cyber and data protection risk - what’s driving the rise, what organisations are doing (or not) to protect themselves and what risk (or help) does generative AI pose.
While data protection compliance issues related to international data transfers, behavioural advertising and AI continue grab considerable amount of DP compliance attention the ransomware fires continue to burn.
The impacts of ransomware can be devasting for organizations and for those people whose personal data is impacted, particularly via exfiltration and publication.
What is ransomware?
Ransomware is a type of malware which prevents you from accessing your device and the data stored on it, usually by encrypting your files. A criminal group will then demand a ransom in exchange for decryption. The computer itself may become locked, or the data on it might be encrypted, stolen or deleted. The attackers may also threaten to leak the data they steal. UK National Cyber Security Centre
Ransomware - what evidence do we have on the number of incidents?
Not all data points towards a unanimous picture of ransomware incidents increasing, but looking across the various datasets, from the UK and globally, the trends indicate that ransomware is rising as a risk in 2023.
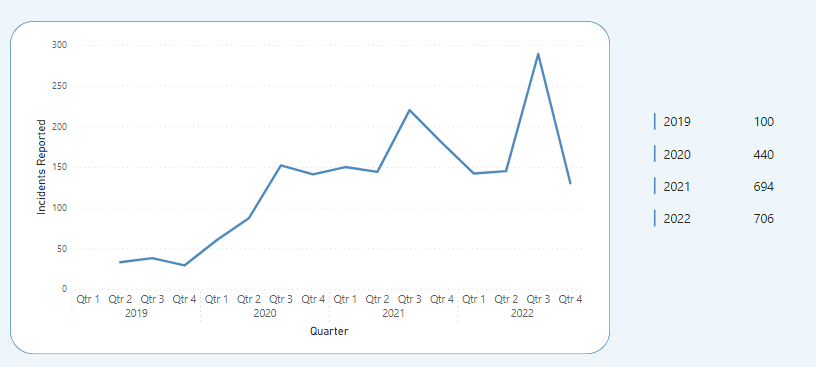
The security incident trends data from the UK Information Commissioner’s Office (ICO), drawn from data about GDPR data breach notifications, paints a picture of ransomware on the rise, a significant increase from 2019 up to 2022. The data also indicates that one in three cyber incidents reported to ICO is ransomware
Of course the ICO data doesn’t reveal the full picture as many ransomware incidents will not be reported. In some cases, where lower risk personal data is encrypted by attackers, but not exfiltrated, and systems quickly restored, it may not be necessary to report under GDPR article 33. This is because although a breach has occurred (availability of personal data) it may not reach the reporting threshold if it does not pose a risk to rights and freedoms of the individual. No doubt some organizations do not report important breaches and simply hope to stay under the radar (a risky approach).
The ICO is also encouraging greater engagement (with the UK National Cyber Security Centre) and openness about data breaches, and can recognize this a factor in their fining process:
“Specifically, the Commissioner will publicise (on its website, in guidance, and in relevant press releases) that it looks favourably on victims of nationally significant cyber incidents who report to and engage with the NCSC and will consider whether it can be more specific on how such engagement might factor into its calculation of regulatory fines.” (New ICO-NCSC MOU, September 2023)
In the UK we have several sources of data to consider. The UK Government’s Cyber Security Breaches Survey, is run annually. Although voluntary it provides a snapshot of the cyber risks that UK businesses face and how they are changing over time. It’s also useful to note that this survey has a much greater degree of reliability than many of the commercial cyber breach surveys out there (usual from software vendors) as there is data provided about the statistical reliability of the survey. DSIT’s data paints a different picture to the ICO’s on ransomware: a fall in ransomware attacks from 17% of all incidents in 2020 to just 4%. Writing in The Record, Alexander Martin suggests the difference between the breach survey and the ICO’s data can be explained by the voluntary nature of the survey and that organizations who have suffered an incident will often choose not to respond or reveal the incident (his article also has an excellent deeper dive into the ICO data).
There are also a number commercial surveys that indicate a rise:
Veeam’s 2023 Ransomware Trends Report of 1200 IT leaders globally indicated a rise of 12%.
NCC Group’s threat pulse indicates that July 2023 saw record levels of ransomware attacks carried out. 502 were observed by NCC In July. The findings mark a 154% increase year-on-year.
In August 2023 Malwarebytes found that a total of 48 separate ransomware groups attacked the US in the observed period. There was a 75 percent increase in the average number of monthly attacks in the US between the first and second half of the last 12 months.
However, there is not one single study that can claim to fully capture the current situation with ransomware attacks, given the number of variables that influence whether an organization wishes to reveal they are a victim.
In a new joint advisory the UK, United States, Australia, Canada, France, Germany and New Zealand revealed that Lockbit was the most deployed ransomware variant across the world in 2022.
Paying the price?
Despite repeated advice from regulators and government cyber advice teams against paying ransoms some victims of ransomware attacks are continuing to pay up.
The US Department of Homeland Security’s Threat Assessment report released in September highlighted the growth of the risk from ransomware. Noting that ransomware attackers extorted at least $449.1 million globally during the first half of 2023 and are expected to have their second most profitable year.
In July of this year Wired reported data from cryptocurrency tracing firm Chainalysis - this indicated that victims paid ransomware groups $449.1 million in the first six months of this 2023. This has already exceeded the figure for 2022. While noting that a snapshot of crypto data can’t be used as a sole indicator, combined with other data it does indicate that ransom payments are increasing.
The 2023 UK Government Cyber Breach Survey revealed the following in terms or organisational policies on paying ransoms:
“Just over half of businesses (57%) have a rule or policy to not pay ransomware payments – this is in line with last year, when this question was introduced. However, there is still a high level of uncertainty among organisations on this topic, with two in ten of the responsible individuals in businesses (21%) and three in ten in charities (28%) saying they do not know what their organisation’s policy is.”
Having a clear policy on not paying ransoms can set an important message for the cyber security culture and approach of the organisation.
The UK National Cyber Security Centre and the UK ICO wrote an open letter to the Law Society in 2022. The letter made clear that paying ransoms to release encrypted data does not reduce the risk to individuals and isn’t a reasonable compliance step under GDPR. Plus the ICO makes it clear it will not be a mitigating factor when considering a GDPR fine or other enforcement action.
The same message comes from the US government: The #StopRansomware Guide, which is issued by the Cybersecurity and Infrastructure Security Agency (CISA), FBI, National Security Agency (NSA), and Multi-State Information Sharing and Analysis Center (MS-ISAC), also makes clear:
“paying ransom will not ensure your data is decrypted, that your systems or data will no longer be compromised, or that your data will not be leaked.”
The guide also warns of sanction risks, as paying ransoms to certain actors could fall within the U.S. Department of the Treasury Office of Foreign Assets Control (OFAC) memorandum.
Why are the the attacks increasing?
The Wired article (referenced above) also quotes Chainalysis on the possible reasons - suggesting that the Russia-Ukraine conflict has impacted the numbers: “actors have settled into safe locations, whether their year of military service has finished, or whether perhaps there’s a mandate to release the hounds.”
We can also see that Ransomware-as-a-Service (RaaS) is on the rise. Fortinet describes it in the following way: “Ransomware-as-a-Service (RaaS) refers to a subscription-based ransomware system, one that enables inexperienced cyber criminals to launch ransomware attacks.” This further reduces the barriers to entry for criminals. As noted below we also have the potential of AI to add into the mix as well.
LockBit (mentioned above as the leading ransomware threat in 2023) runs on a RaaS model. LockBit ransomware attacks have a wide variance in the observed tactics, techniques, and procedures (TTPs) used.
Also in heavy use, the Russian group Cl0p took advantage of a previously unknown flaw in MOVEit Transfer, a digital tool used by businesses around the world to securely share documents. Indications are that over 400 organizations have been impacted. Indications are that Cl0p offers a RaaS mode and will rent the software to affiliates.
What are the impacts of ransomware?
Impacts of ransomware can include:
Impacts on people - fraud risks from data publication on the dark web, distress caused by intrusion into sensitive data, even if not infiltrated.
Loss of internal and external digital services due to data encryption. This can cause a loss of customers and revenue, impacts on productivity, impacts of reputation and trust in the service. The time and cost of restoring such services can also be considerable.
The costs of incident management, investigation and recovery.
Impacts on reputation and share price.
Impacts on business customers from breaches to the confidentiality of information.
Risks to company assets and intellectual property.
The UK Royal United Services Institute (RUSI) is working on a project that looks at ransomware harms and the victim experience, illustrating a wide range of harms and should look well beyond the well known impacts on service availability etc. An important study to watch out for.
When to notify ransomware incidents as GDPR breaches to the DPA
Organizations will have to consider a range of factors to work through the breach notification process related to ransomware (under Article 33 GDPR).
Has the controller become aware of a personal data breach? - do they have a reasonable degree of certainty (see EDPB guidance).
Discovery of intrusion and encrypted data - is personal data compromised? and What is the level of sensitivity? Only certain portions of a server may be compromised and it may be necessary to use a back up to help the assessment. Does the unavailability of the encrypted data present a risk to individuals? E.g health records or personal banking systems are unavailable via a health portal for many days.
Discovery of evidence of exfiltration - has all the encrypted data been exfiltrated or just a portion? What is the potential to risks individuals from this additional step?
Discovery that exfiltrated data has been de-crypted posted on an open forum - The availability of the personal data on forums such as the dark web will also require an assessment of risk, from the perspective of a confidentiality breach.
Alongside the encryption and exfiltration aspects there can also be further issues as to whether attackers have been able to amend or delete personal data, therefore the risks associated with an integrity breach.
Are EU and UK Data Protection Authorities (DPAs) taking enforcement action related to ransomware incidents?
The number of fines issued so far are relatively small but DPAs are clearly investigating and the more serious cases of non-compliance with Articles 5, 32, 33 and 34 GDPR are attracting sanctions.
We can note the following cases so far.
UK ICO. Tuckers Solicitors were fined £98,000 is 2022 for breaches of GDPR related to a ransomware attack. 972,191 individual files were encrypted, including 60 court bundles were exfiltrated by the attacker and published on an underground market site. The bundles included special category data personal data, such as medical files, witness statements, names, addresses of witnesses and victims, and the alleged crimes. Tuckers did not use multi-factor authentication for remote access to their systems, despite this being recommended for solicitors since 2018.
UK ICO. Construction company Interserve were fined £4.4 million in 2022 for breaches of GDPR related to a ransomware attack. Data compromised included employees’ contact details, national insurance numbers, and bank account details, as well as special category data including ethnic origin, religion, details of disabilities, sexual orientation, and health information. Interserve failed to follow-up on the original alert of a suspicious activity, used outdated software systems and protocols, and had a lack of adequate staff training and insufficient risk assessments
Norwegian DPA fined a municipality €409,768 for breaches of GDPR after a serious ransomware attack led to highly sensitive personal data being irreparably lost and sold on the dark web.
Key findings from these enforcement actions covered the following:
Poor patch management and out of date updates in use;
Lack of encryption, which could have mitigated risk;
Weaknesses of remote access systems;
Lack of Multi-Factor Authentication;
Unsecured back up and lack of log files;
Ineffective alerting mechanisms for phishing and malware;
Inadequate staff training and system.
The most significant ransomware investigation currently underway at the UK ICO is focused on the Capita ransomware incident (March 2023), that involves over 90 different organisations who use Capita’s services for functions such as pensions and payroll. The ICO has therefore received significant numbers of individual breach notifications and will need to investigate from a number of perspectives, looking at Capita and the organisations who used the services. The attack has come from the Black Basta ransomware group, who attacked Capita’s Office 365 software. Capita also report that they expect to incur exceptional costs of approximately £15m to £20m associated with the incident. Capita have also reported that data was only exfiltrated from less than 0.1% of its server estate. Pension providers may also need to notify the Pensions Regulator as well as the ICO.
Guidance and resources
There is lots of guidance to support organisations in how their security management programmes effectively address the risks of ransomware.
Essential reading:
UK NCSC ransomware guidance. Four key steps:
Action 1: make regular backup
Action 2: prevent malware from being delivered and spreading to device
Action 3: prevent malware from running on device
Action 4: prepare for an incident
US Government: Stop ransomware guidance
UK ICO guidance: organisations must regularly monitor for suspicious activity and investigate any initial warnings; update software and remove outdated or unused platforms; update policies and secure data management systems; provide regular staff training; and, encourage secure passwords and multi-factor authentication.
ENISA (EU) - Prevention response for ransomware attacks
Will AI help or make things worse?
AI will help detect and prevent ransomware attacks and a number of providers, such as Microsoft, are offering AI based solutions to enhance cyber security solutions on offer.
Against this is the concern that AI can act as an accelerant for ransomware attacks. The premise is that generative AI tools could enable less skilled actors to develop code and initiate attacks or speed up the process of developing the code and tools needed for attacks. A major concern is that attackers could automate ransomware using AI to allow them to go after an even wider range of targets. Speaking to Protocol, cyber security expert Mikko Hyppönen indicated that AI could automate some of the attackers tasks but not all:
“Monitoring systems, changing the malware code, recompiling it and registering new domain names to avoid defenses — things it takes humans a long time to do — would all be fairly simple to do with automation. All of this is done in an instant by machines”
“The actual execution of a ransomware attack remains difficult”
It all depends how much more efficient AI will be for attackers and whether it is worth the time, costs and effort. Attackers are still likely to have make corrections to code from generative AI systems, though this will improve. There are already examples emerging of how generative AI can write malware. But the question is how much that helps a novice without other knowledge on execution of a full attack.
Mainstream generative AI services are also seeking to place filters to stop the relevant prompts, but there will be workarounds, as researchers have demonstrated.
OpenAI’s safety card for ChatGPT 4 sets out their current assessment of cyber risks. As part of this process they contracted external cyber security experts to test GPT-4’s ability to aid in computer vulnerability discovery, assessment, and exploitation. They found that GPT-4 “performed poorly at building exploits for the vulnerabilities that were identified”. GPT4 did not do well at enumerating targets and using more recent information (*though this is changing with the new feature to browse the latest web data - the added functionality will be available to ChatGPT Plus and Enterprise subscribers). ChatGPT did perform well in providing phishing and social engineering content.
Use of AI in ransomware negotiations is also possible - attackers may seek to negotiate using generative AI chat tools, therefore enabling many simultaneous negotiations, and greater precision and learning in their tactics. Generative AI could also improve the plausibility of of the information provided.
This NCSC blog also provides a good overview of the cyber risks related to generative AI.
The hope is that AI defences can stay one step ahead of how attackers utilise AI but we will see how this pans out over the next few years.
Ransomware protection still comes down to rigorous application of security lifecycle management and the combination of people, policies, procedures, training and the right technical tools - matched to the specific risks posed by ransomware that organisations (and their partners) regularly review and assess - that will continue to make a difference.
PrivacyX updates: what I’m currently up to….
I’m currently working on the following projects:
Supporting a government project on the implementation of a new data protection law and new data protection regulator (Africa).
A policy project on the metaverse, immersive environments and data protection compliance.
Advice on age assurance and age appropriate design.
With my Visiting Policy Fellow hat on (at the Oxford Internet Institute), I’m also working on an academic article about the impacts of social recommender systems on children and how this interacts with forthcoming systems of regulation.
Where I’ll be this autumn
I’m looking forward to getting out and about this autumn and I’ll be at the following events.
Asia Privacy Bridge Forum, Seoul, 11-13 October. I’ll be giving a keynote speech about Generative AI and Data Protection.
Global Privacy Assembly Annual Conference Bermuda, 16-19 October
Oxford Generative AI Summit 2023, 21 October. Oxford. I’ll be moderating a panel on Generative AI and data protection.
IAPP Europe Data Protection Congress 2023. 14-16 November. Brussels. Listening and networking.
ILPC Annual Conference 2023 Human in the Machine: Digital Rights and AI, London, 23 November. Keynote presentation.
Other publications
You can also find more information about other articles and publications I’ve written.
Re-use and copyright
If you would like to re-use the article content and/or the infographic they are available under a Creative Commons BY-NC license. This allows re-users to distribute, remix, adapt, and build upon the material in any medium or format for noncommercial purposes only, and only so long as attribution is given to the creator.